which of the following categories require a privileged access agreement
Cybersecurity is not a holistic program to manage Information Technology related security risk. To know who has access to these accounts you must enter all relevant applications on the network and then identify the privileged access service or proxy accounts that.

Understanding Privileged Access Management Pam Strongdm
This test can only be attempted once every 60 minutes.
. System administrators need to do a lot of different. Individuals only after they have read and signed this Agreement. Privileged access enables an individual to take actions that may affect computing systems network communication or the accounts files data or processes of other users.
However the best approach for each organization is. Why can melted paraffin drop a certain height and not just rub on the skin. Devices must be configured with separate accounts for privileged administrator and non-privileged user access.
Define baselines for privileged user activity and privileged access and monitor and alert any deviations that meet a defined risk threshold. Precursors and actions 2. IA Technical requires a privileged access agreement.
Many organizations have a similar path to maturity eligibility prioritizing first simple profits and the greatest risks and then gradually improving preferred security controls across the enterprise. IA Technical requires a privileged-level access agreement. IA Technical requires a privileged level access agreement.
Lost and found c. Indications and precursors b. Silahkan tuliskan komentar Anda yang sesuai dengan topik postingan halaman ini.
Cyber Security Fundamentals 2020 Pre-Test This exam works as a test out function for the training and will result in a certificate upon completionYou must earn an 80 or above to pass. Which of the following Categories Require a Privileged-Level Access Agreement. Therefore the idea of specific categories doesnt really apply here.
Types of commercial off -the-shelf operating systems. Which of the following categories require a privileged access agreement. Get 60 minutes online personalized tutoring session for each theme of all university tutor notes.
Integrate other risk data for a more three-dimensional view of privilege risks. Individuals are also required to keep. A system adminstrator is issued privileged and non-privileged user accounts.
Implement threatprivileged user analysis. Collecting as much data as possible is not necessarily the solution. Nel who require privileged accesselevated privileges to Army Information Systems.
Restricting privi leged accounts to specific personnel or roles prevents. Any time private information is shared a master user must decide which other users may be privy to the information and how. Which of the following categories requires a privileged access agreement.
Your data including personal data is safe with us. Which of the following categories require a privileged access agreement. Cybersecurity is not a holistic program to manage Information Technology related security risk.
Komentar yang berisi tautan tidak akan ditampilkan sebelum disetujui. What is a privileged access agreement. This answer was confirmed as correct and useful.
This answer was confirmed as correct and useful. Indications of an incident fall into two categories a. In accordance with AR 25-2 whose responsibility is it to ensure all users receive initial and annual IA awareness training.
We select pages that contain information about categories that require a privileged access agreement. If the following categories require a preferred level access agreement. If you own a training company youre probably always looking for new ways to increase the number of participants.
You can also reduce the time you spend on administrative tasks related to training submissions to spend more time on value-added tasks. There can be a privileged-level access agreement for almost any sort of computer system contract document or software application. This includes the official login link and all the login information tips and requirements.
Personnel with privileged access must complete a Privileged Access Agreement. Worms and Trojan horses are types. Which categories require a privileged access agreement.
Individuals with privileged access must respect the rights of system users respect the integrity of systems and associated physical resources and comply with all relevant laws or regulations. Which of the following certifications would satisfy IAM level II and IAM level III. This is an example of applying the principle of least privilege.
Understand Admin Access And Rbac Policies On Ise Cisco

Privileged Access Management Senhasegura
Understanding Privileged Access Management Pam Strongdm

What Is Privileged Access Management Pam Explained Security Wiki
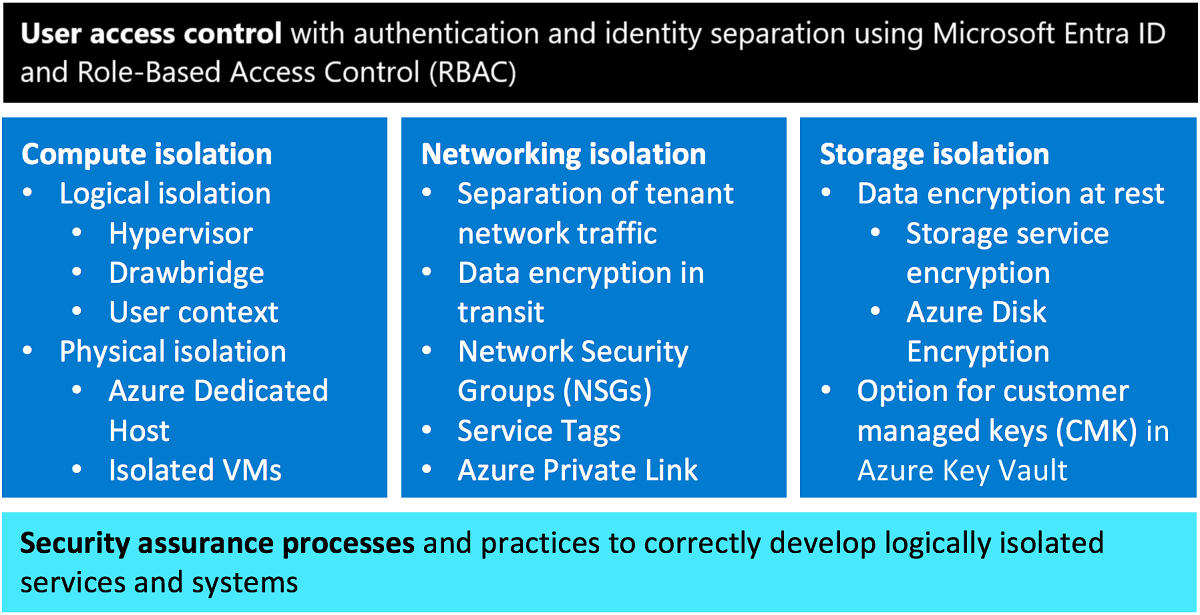
Azure Guidance For Secure Isolation Azure Government Microsoft Docs

Omdia Universe Selecting A Privileged Access Management Solution 2021 22 Omdia
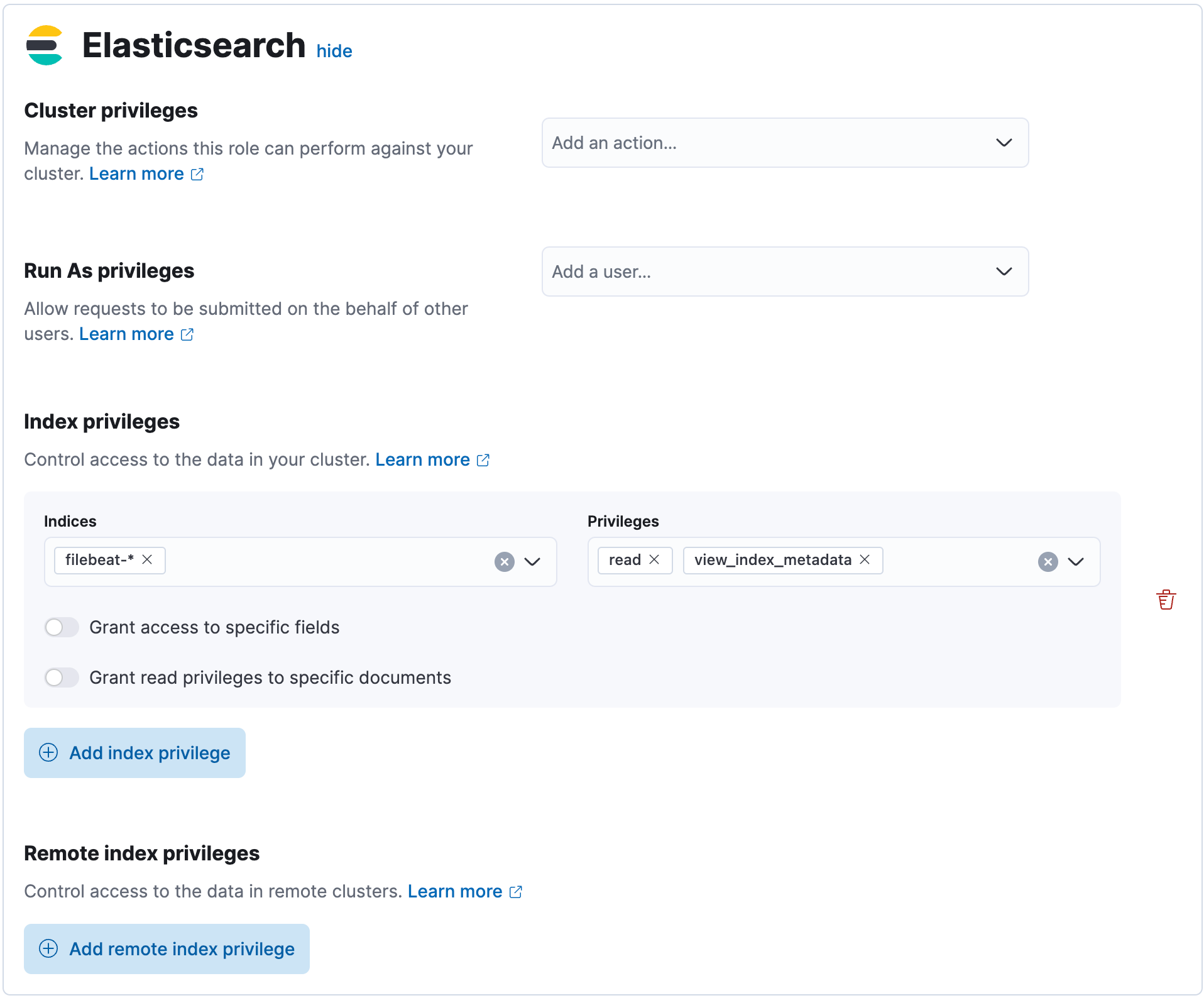
Kibana Role Management Kibana Guide 8 2 Elastic

Edtechsandyk Byod Equity Panel At Sxswedu 2014 Byod Teacher Classroom Equity

Solutions Cisco Secure Access Service Edge Sase With Meraki Sd Wan Design Guide Cisco
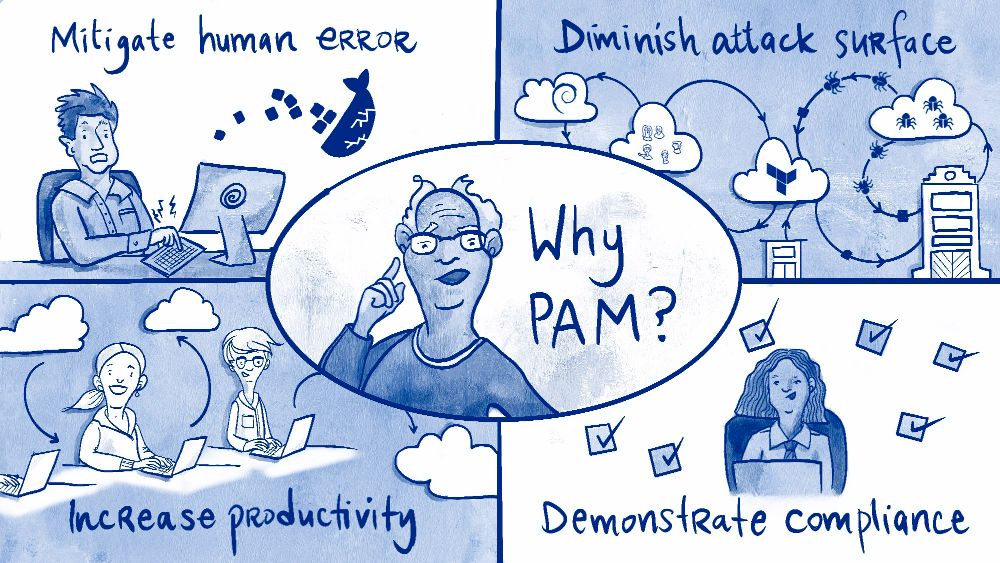
Understanding Privileged Access Management Pam Strongdm
What Is Privileged Access Management Pam Explained Security Wiki

Iam Vs Pam Know The Difference

Powerful Privileged Access Management Cloud Or On Premises
Knowledge Base Article Service Portal